Deploy Copilot AI Without Fear
Fear is expensive. While competitors hesitate, smart organizations are already leveraging Microsoft Copilot to transform operations, accelerate decision-making, and drive innovation. The difference? They understand that proper security enables AI adoption rather than preventing it.
The Cost of AI Hesitation
Organizations delaying Microsoft Copilot deployment due to security concerns are falling behind measurably. Recent studies show companies using AI tools like Copilot report 26% faster task completion and 44% higher accuracy across security operations. Meanwhile, hesitant organizations watch competitors pull ahead in productivity, customer service, and operational efficiency.
Why Smart Organizations Move Forward
Smart organizations recognize that AI security isn’t about eliminating all risk—it’s about managing risk intelligently while capturing competitive advantages. They deploy Microsoft Copilot with confidence because they’ve implemented proper security frameworks that enable innovation rather than stifle it.
The Real Risk of Waiting
Every month of delayed AI adoption represents lost opportunities. While you evaluate security concerns, competitors are training their teams on AI-enhanced workflows, optimizing business processes, and building AI-native capabilities that will be difficult to match later.
Building Confidence Through Security Architecture
Essential Security Foundations
Data Classification and Boundaries
Before deploying Copilot, establish clear data boundaries. Identify which information types require protection and implement access controls that prevent unauthorized exposure. We implement data classification frameworks that secure sensitive information without limiting AI functionality.
Identity and Access Management
Configure robust authentication controls that verify user identity before granting Copilot access. Multi-factor authentication, conditional access policies, and proper permission structures ensure only authorized users can interact with AI systems. These controls build confidence by providing clear visibility into who accesses what information.
Content Filtering and Prompt Validation
Implement intelligent content filtering that prevents sensitive information from being processed inappropriately while maintaining Copilot’s analytical capabilities. Smart content filters distinguish between legitimate business queries and potentially risky prompts, allowing productive AI interactions while blocking dangerous ones.
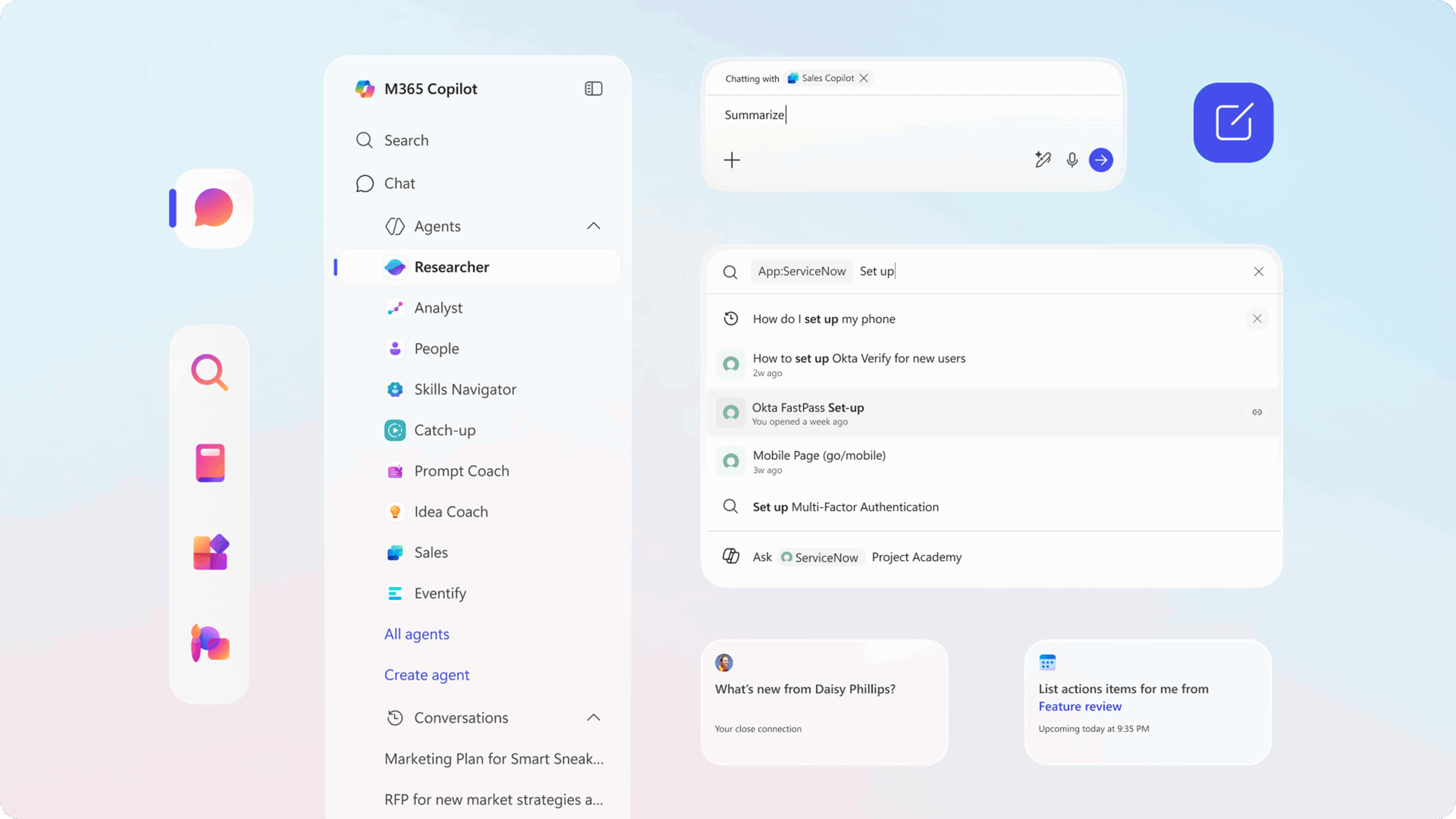
Advanced Security Configurations
Microsoft Copilot Studio Protection
Secure custom agent development through proper Copilot Studio configurations. Implement approval workflows for new agents, establish testing environments for agent validation, and maintain audit trails of all agent interactions. We protect Copilot Studio environments while preserving development flexibility.
API Security and Governance
The M365 Copilot API requires careful security configuration to prevent unauthorized data access. Implement proper API authentication, establish rate limiting to prevent abuse, and monitor API interactions for suspicious patterns. These controls ensure Copilot integrations remain secure without limiting functionality.
Smart Deployment Strategies That Eliminate Fear
Successful Microsoft Copilot deployments follow proven patterns that build confidence through measured, secure implementation. Smart organizations don’t deploy AI everywhere at once—they start strategically and expand systematically.
Phase 1
Pilot with High-Value, Low-Risk Use Cases
Begin Copilot deployment with business functions that offer significant value but handle less sensitive data. Marketing content creation, routine administrative tasks, and general business analysis provide excellent starting points for building AI confidence without exposing critical information.
Phase 2
Expand to Core Business Functions
Once initial security controls prove effective, expand Copilot access to core business functions. Sales support, customer service enhancement, and operational optimization represent the next logical expansion areas where AI delivers measurable business impact.
Phase 3
Strategic Integration Across Enterprise
The final phase involves enterprise-wide Copilot integration with full security governance. This includes financial analysis, strategic planning support, and executive decision-making assistance—all protected by mature security frameworks developed during earlier phases.
Governance Frameworks That Enable Innovation
Clear Microsoft Copilot Usage Policies
Establish comprehensive but practical usage policies that guide employee interactions with Copilot. These policies should encourage productive AI use while clearly defining boundaries around sensitive information handling. Well-designed policies reduce anxiety by providing clear guidance rather than restrictive barriers.
Continuous Monitoring and Improvement
Implement monitoring systems that track Copilot interactions, identify potential security issues, and measure business value delivery. This ongoing visibility builds confidence by demonstrating that security controls are working effectively while AI delivers promised benefits.
Training and Change Management
Provide comprehensive training that builds both AI competency and security awareness. Employees who understand how to use Copilot securely are more likely to embrace AI tools confidently, driving faster adoption and better business outcomes.
Addressing Common Security Concerns
Many organizations delay Copilot deployment due to misconceptions about AI security risks. Understanding these concerns and implementing appropriate controls eliminates fear while preserving the caution necessary for responsible AI adoption.
Data Leakage Prevention
Prompt Injection Protection
Modern prompt injection attacks attempt to manipulate AI responses to reveal sensitive information. Smart organizations implement validation systems that detect suspicious prompts while allowing legitimate business queries. These protections operate transparently, maintaining user experience while preventing data exposure.
Response Filtering and Sanitization
Configure Copilot to filter responses that might contain sensitive information inadvertently included from connected systems. Intelligent response filtering preserves AI analytical capabilities while preventing accidental data disclosure through AI-generated content.
Compliance and Regulatory Alignment
Industry-Specific Requirements
Healthcare, financial services, and defense organizations face unique compliance challenges with AI deployment. Smart organizations address these requirements proactively through industry-specific security configurations that maintain regulatory compliance while enabling AI innovation.
Audit Trail and Documentation
Comprehensive audit trails demonstrate compliance with regulatory requirements while providing visibility into AI usage patterns. These documentation systems build confidence with auditors and executives by proving that AI deployments meet all necessary compliance standards.
Competitive Advantages of Fearless AI Adoption
Organizations that deploy Microsoft Copilot confidently gain measurable advantages over competitors still paralyzed by security concerns. These advantages compound over time as AI-enhanced operations become increasingly sophisticated.
Operational Efficiency Gains
Accelerated Decision-Making
Copilot-enhanced analysis enables faster, more informed decision-making across the organization. While competitors manually analyze data, smart organizations leverage AI to process information quickly and identify opportunities others miss.
Enhanced Employee Productivity
Teams using Copilot complete tasks faster and with higher accuracy, freeing time for strategic initiatives that drive business growth. This productivity improvement becomes a sustainable competitive advantage as AI capabilities continue expanding.
Innovation and Market Responsiveness
Rapid Adaptation to Market Changes
AI-enhanced organizations respond faster to market shifts, customer needs, and competitive threats. Copilot provides analytical capabilities that help identify trends and opportunities before competitors recognize them.
Customer Experience Enhancement
Copilot-powered customer service and support deliver superior experiences that drive customer loyalty and retention. These improvements translate directly into competitive advantages in customer satisfaction and market share.
The Security-Innovation Balance
Smart organizations understand that Microsoft Copilot security and innovation aren’t opposing forces—they’re complementary capabilities that together enable sustainable competitive advantages. Proper security provides the confidence necessary for bold AI adoption, while AI capabilities drive the business results that justify security investments.
Building Long-Term AI Capabilities
Scalable Security Architecture
Design security frameworks that grow with AI adoption rather than constraining it. Scalable architectures support expanding AI use cases while maintaining consistent protection standards across the organization.
Continuous Security Evolution
AI threats and capabilities evolve rapidly, requiring security approaches that adapt accordingly. Smart organizations implement flexible security frameworks that can incorporate new protections without disrupting existing AI workflows.
Microsoft Copilot
Frequently Asked Questions
What security risks do Microsoft 365 Copilot and AI Agents introduce?
Microsoft 365 Copilot and AI Agents create new security risks. The attack vectors include data leakage through prompt injection, oversharing of sensitive information in AI responses, and unauthorized access to organizational data through compromised AI interactions. The Researcher and Analyst agents can inadvertently expose confidential business intelligence if not properly secured. We secure Copilot and identify these vulnerabilities before they become breaches.
https://www.youtube.com/watch?v=rAg64tgoW6UCopilot Security Risks Organizations Face
The core problem: Microsoft Copilot honors existing SharePoint permissions while dramatically expanding data discovery through AI-powered search and correlation. Minor permission oversights become major Microsoft AI security breaches.
Microsoft's Proven Copilot Security Framework
Rather than blocking Microsoft AI deployment, the Cloud Solution Architect recommends systematic Copilot security implementation that enables confident artificial intelligence adoption.
Phase 1: Microsoft AI Security Assessment
Engage Microsoft 365 administrators including SharePoint, Compliance, and Copilot security teams for comprehensive AI protection coverage.
Define Microsoft AI sensitivity standards by establishing clear Copilot data classification criteria that prevent artificial intelligence overexposure.
Discover Copilot data access patterns using SharePoint Data Access Governance reports to identify Microsoft AI security vulnerabilities.
Phase 2: Copilot Security Implementation
Prioritize Microsoft AI data protection by securing the most sensitive Copilot-accessible information first through targeted artificial intelligence security controls.
Deploy Microsoft Purview solutions that provide ongoing Copilot security rather than one-time Microsoft AI protection fixes.
Ready for Secure Microsoft AI Implementation?
Don't let Copilot security concerns delay competitive advantages through Microsoft AI adoption. Proven artificial intelligence frameworks enable confident deployment with comprehensive data protection. Protect AI ToolsHow can organizations secure Copilot Studio deployments and custom agents?
Copilot Security Risks Organizations Face
The core problem: Microsoft Copilot honors existing SharePoint permissions while dramatically expanding data discovery through AI-powered search and correlation. Minor permission oversights become major Microsoft AI security breaches.
Microsoft's Proven Copilot Security Framework
Rather than blocking Microsoft AI deployment, the Cloud Solution Architect recommends systematic Copilot security implementation that enables confident artificial intelligence adoption.
Phase 1: Microsoft AI Security Assessment
Engage Microsoft 365 administrators including SharePoint, Compliance, and Copilot security teams for comprehensive AI protection coverage.
Define Microsoft AI sensitivity standards by establishing clear Copilot data classification criteria that prevent artificial intelligence overexposure.
Discover Copilot data access patterns using SharePoint Data Access Governance reports to identify Microsoft AI security vulnerabilities.
Phase 2: Copilot Security Implementation
Prioritize Microsoft AI data protection by securing the most sensitive Copilot-accessible information first through targeted artificial intelligence security controls.
Deploy Microsoft Purview solutions that provide ongoing Copilot security rather than one-time Microsoft AI protection fixes.
Ready for Secure Microsoft AI Implementation?
Don't let Copilot security concerns delay competitive advantages through Microsoft AI adoption. Proven artificial intelligence frameworks enable confident deployment with comprehensive data protection. Protect AI ToolsWhat are the biggest data leakage risks with Microsoft Copilot interactions?
The primary data leakage risks include employees accidentally sharing sensitive information in prompts, Copilot responses containing confidential data from connected systems, and unauthorized data access through poorly configured agent permissions. Code Interpreter functions can expose proprietary algorithms, while CUA (Conversational User Authentication) bypasses may grant excessive access. We prevent data loss across all AI interactions.
What compliance challenges do Microsoft AI Agents create for regulated industries?
AI Agents introduce compliance complexities around data residency, audit trail requirements, and regulatory approval processes. The M365 Copilot API can create data flows that violate industry regulations if not properly configured. Healthcare, financial, and defense organizations face particular compliance challenges with agent-generated content and automated decision-making processes. We address regulatory requirements for AI implementations.
How should organizations govern and secure agents from the Agent Store?
How can organizations tune M365 Copilot to reduce security risks while maintaining functionality?
Copilot Security Risks Organizations Face
The core problem: Microsoft Copilot honors existing SharePoint permissions while dramatically expanding data discovery through AI-powered search and correlation. Minor permission oversights become major Microsoft AI security breaches.
Microsoft's Proven Copilot Security Framework
Rather than blocking Microsoft AI deployment, the Cloud Solution Architect recommends systematic Copilot security implementation that enables confident artificial intelligence adoption.
Phase 1: Microsoft AI Security Assessment
Engage Microsoft 365 administrators including SharePoint, Compliance, and Copilot security teams for comprehensive AI protection coverage.
Define Microsoft AI sensitivity standards by establishing clear Copilot data classification criteria that prevent artificial intelligence overexposure.
Discover Copilot data access patterns using SharePoint Data Access Governance reports to identify Microsoft AI security vulnerabilities.
Phase 2: Copilot Security Implementation
Prioritize Microsoft AI data protection by securing the most sensitive Copilot-accessible information first through targeted artificial intelligence security controls.
Deploy Microsoft Purview solutions that provide ongoing Copilot security rather than one-time Microsoft AI protection fixes.
Ready for Secure Microsoft AI Implementation?
Don't let Copilot security concerns delay competitive advantages through Microsoft AI adoption. Proven artificial intelligence frameworks enable confident deployment with comprehensive data protection. Protect AI ToolsCan Copilot leak data into the model or generate something sensitive by accident?
No, Copilot does not train on organizational data or leak information into the model. Each organization has their own instance of the AI and Large Language Model (LLM). Customer A's LLM is completely separate from Customer B's LLM. Copilot consists of three components: the LLM, semantic index, and Microsoft Graph, but all data stays within the organization's instance and is never used for training purposes. Our Microsoft AI security framework ensures complete data isolation.
What’s the safest way to roll out Copilot to multiple teams without rushing it?
This seems really complicated. Can managed service providers help with Copilot implementation?
Will Microsoft Purview and DLP policies work with other AI models beyond Copilot?
Absolutely. If building AI solutions with Azure Foundry or other models within the Microsoft ecosystem, Purview capabilities apply across all Microsoft workloads. All classification, labeling, and data governance features available with Microsoft 365 Copilot extend to broader Azure components and custom LLM implementations that leverage Microsoft Graph. Our Microsoft security integration covers the complete AI ecosystem.
We don’t have E5 licenses but use ChatGPT and are testing Copilot. What are our risk mitigation options?
How can I restrict the Graph to prevent sensitive emails from being leaked through Copilot?
Why is my sensitivity labeling button grayed out in Word when I have a Copilot license?
When Copilot fetches data from SharePoint and OneDrive through Microsoft Graph, can other users’ emails or files be leaked?
What training resources does Microsoft offer for SharePoint Advanced Management?
What about the new Microsoft AI agents – how do they work with security?
Secure AI Deployment
The organizations gaining competitive advantages through Microsoft Copilot aren’t reckless—they’re strategic. They’ve implemented security frameworks that enable confident AI adoption while protecting what matters most.
Don’t let security concerns delay your AI transformation. Smart deployment strategies eliminate fear while preserving the caution necessary for responsible AI adoption. The competitive advantages are real, measurable, and growing every day.
Start your secure Copilot deployment →
For comprehensive answers to common AI security questions, explore our expert resources on artificial intelligence security and AI-enhanced phishing protection.







